The core goals of cryptography and any application of cryptography are confidentiality, integrity, and authenticity. Let's begin with a short one liner on each:
- Confidentiality: No one should be able to read the contents of the message except the intended recipient.
- Integrity: No one should be able to tamper with the message without going unnoticed.
- Authenticity: The recipient should be able to confirm that the message indeed came from the sender.
The Problem
Now the problem with using just an encryption algorithm like AES with a non-authenticating mode like CBC is that anyone can change the ciphertext during transmission. And while you might think, "but the modified ciphertext, with high probability, will decrypt to something gibberish", this isn't the right argument because the recipient will have no way of knowing for sure, which is a problem, a huge one.
Secondly, there's also no way of knowing if the message was sent by a person you're expecting it from. It might have come from any middleman intercepting your network and you wouldn't be able to tell a difference. And for this reason, encryption without authentication and integrity completely destroys the purpose of encryption. An example of this in the real world is when you see an error such as the following:
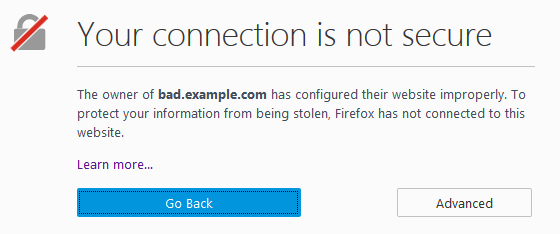 https://support.mozilla.org/en-US/kb/what-does-your-connection-is-not-secure-mean
https://support.mozilla.org/en-US/kb/what-does-your-connection-is-not-secure-mean
While this can mean that the encryption mode used by the website is weak, more often than not, this means that the browser was able to establish a secure connection but the identity of the website is unknown. This defeats the purpose of encryption because even if the connection is secure, the fact that you don't know if you're receiving a message from your intended recipient or if the message hasn't tampered with defeats the purpose of using cryptography.
Enter Authenticated Encryption
Authenticated encryption solves this problem by introducing authentication and integrity as freebies that you get when you use an authenticated encryption mode along with an encryption cipher such as AES. Examples of authenticated encryption modes include GCM and CCM. In fact, if you check the connection info of the site you're reading this on (click the green icon and then select more info or something similar on chrome and firefox) and check the technical details part, you'll see something like this, depending on your browser.
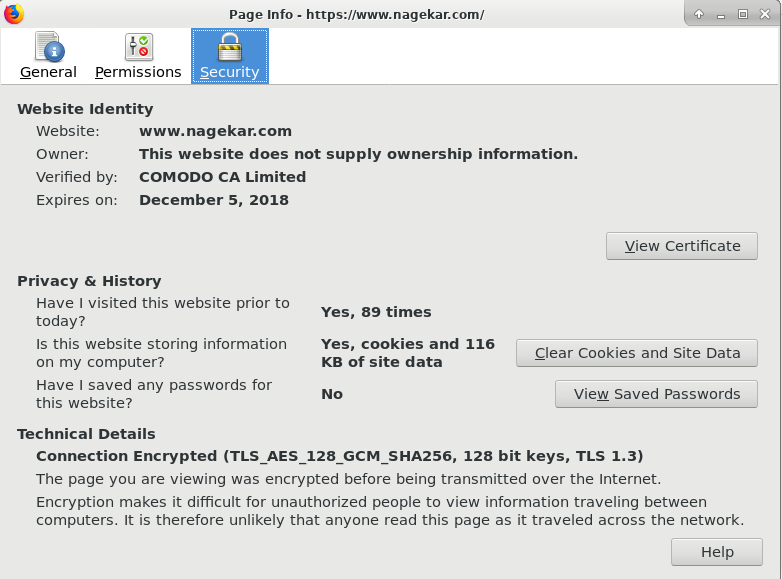 Yes, I'm the most active visitor of my blog
Yes, I'm the most active visitor of my blog
Here, AES_128_GCM is used for symmetric encryption of the content you exchange with the server with AES providing confidentiality and GCM providing authentication and integrity. SHA256 is used to authenticate the initial handshake and as a pseudo-random function (PRF).
In a nutshell, these authenticated encryptions usually take a message, encrypt it, then MAC the ciphertext (and IV) and then append the MAC to the ciphertext. This is called Encrypt-then-MAC. Now if the ciphertext is changed, the MAC won't match and the receiver can easily discard such messages without having to touch the contents of ciphertext. There are other variations to this method, namely MAC-then-Encrypt and MAC-and-Encrypt, with benefits of going with each although most experts recommend doing Encrypt-then-MAC.
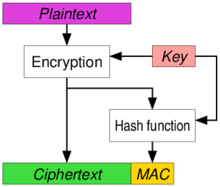
From wikipedia page on authenticated encryption. This is Encrypt-then-MAC
As you can imagine, this can be easily done manually (and until some years ago, it was mostly done by developers). But since it is easier (and much more secure) to standardize such modes and leave the secure implementation part to the experts, these 'readymade' modes have picked up wide adoption and as you saw, you're currently using GCM to ensure confidentiality, integrity, and authenticity of this very line. Thank you for reading!